Secure and Efficient Identity & Access Management (IAM)
Adaptist Prime centralizes Identity and Access Management (IAM) and Identity Governance (IGA) in one unified platform, ensuring only the right users access the right resources at the right time. With Single Sign-On, Multi-Factor Authentication, and automated access workflows, your organization can manage digital identities more securely, efficiently, and in full compliance with regulatory requirements.
Key Feature
Always One Step Ahead of Threats
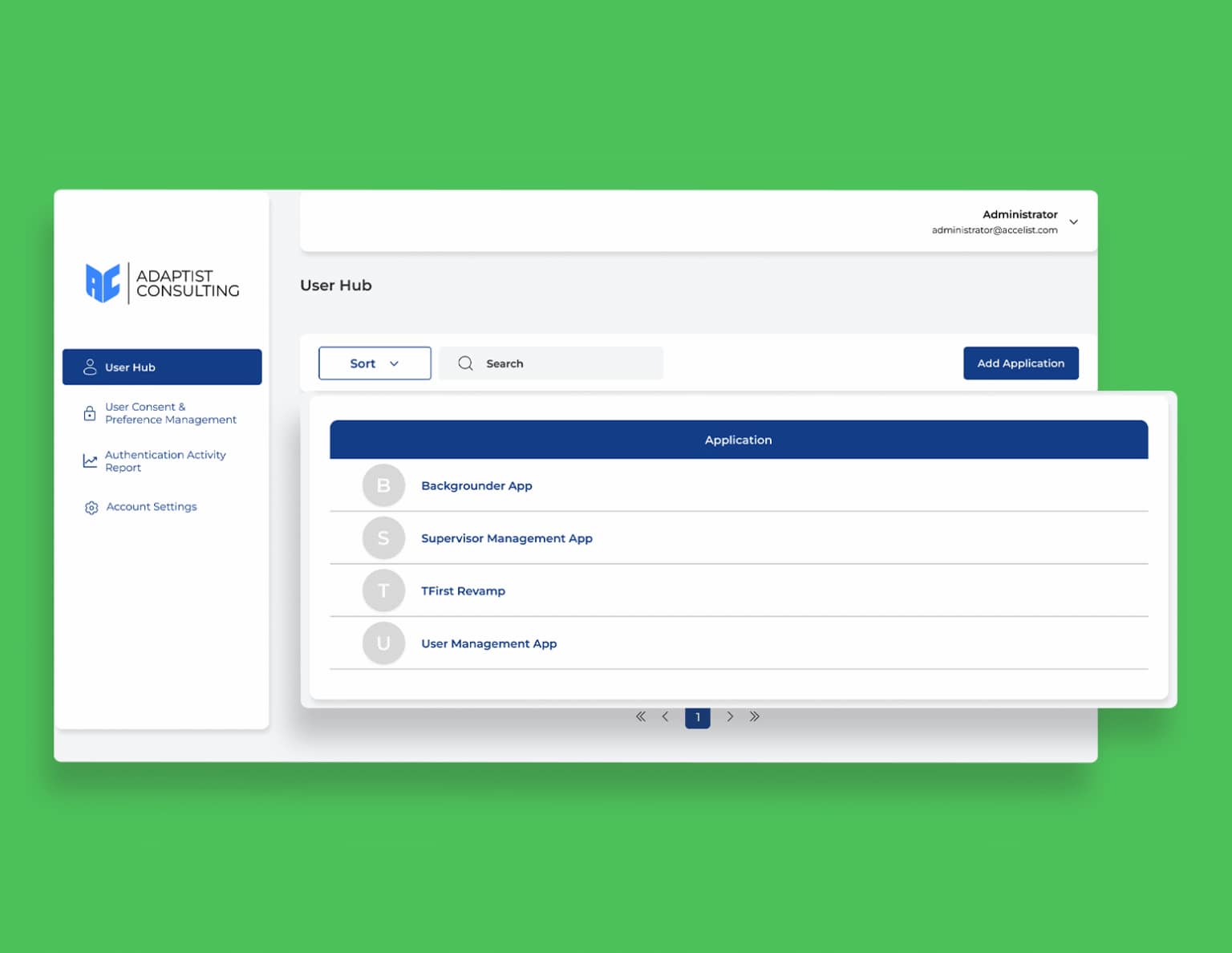
Convenience
Single Sign On
Enjoy the convenience of centralized authentication through Single Sign-On (SSO). With SSO, users only need to log in once to access all integrated applications, without having to remember multiple credentials, as long as the session is still active. This feature not only simplifies the login process, but also enhances security and efficiency. Your organization can reduce the risk of reusing passwords, provide a consistent experience for users, and simplify centralized authentication management. With this approach, access becomes more practical, secure, and remains efficient as your organization's needs evolve
Convenience
Single Sign On
Enjoy the convenience of centralized authentication through Single Sign-On (SSO). With SSO, users only need to log in once to access all integrated applications, without having to remember multiple credentials, as long as the session is still active. This feature not only simplifies the login process, but also enhances security and efficiency. Your organization can reduce the risk of reusing passwords, provide a consistent experience for users, and simplify centralized authentication management. With this approach, access becomes more practical, secure, and remains efficient as your organization's needs evolve

Protection
Conditional Access
Manage access security adaptively and centrally with Conditional Access Rules. This feature allows you to set security levels for each application or user based on specific conditions, such as IP address, location, device, and even Multi-Factor Authentication (MFA) implementation. With this flexibility, organizations can ensure that access is only granted to users who meet the specified criteria, while strengthening protection against security threats. As a result, access control becomes more precise, security remains optimal, and access management can adapt to the evolving needs of your business
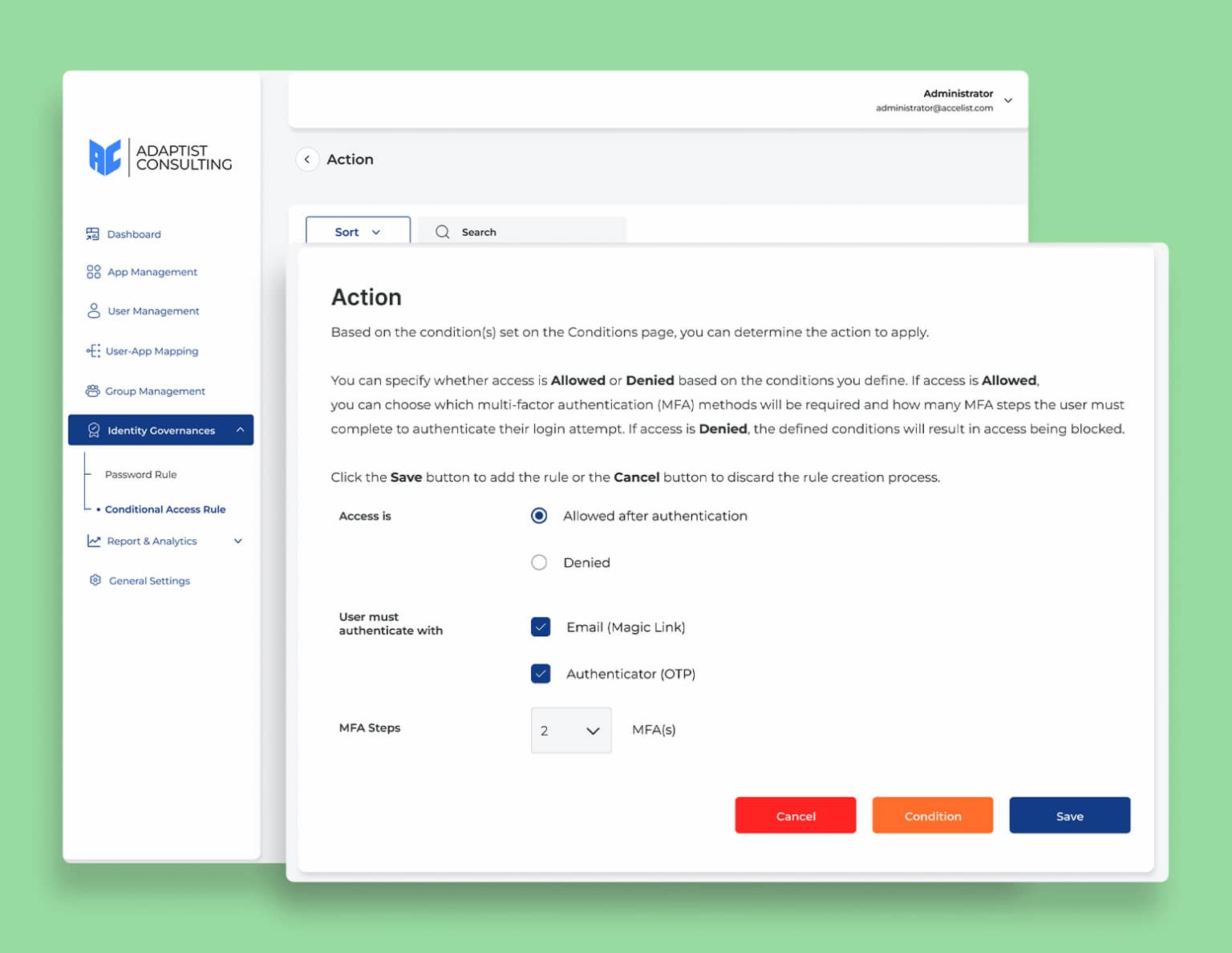
Protection
Conditional Access
Manage access security adaptively and centrally with Conditional Access Rules. This feature allows you to set security levels for each application or user based on specific conditions, such as IP address, location, device, and even Multi-Factor Authentication (MFA) implementation. With this flexibility, organizations can ensure that access is only granted to users who meet the specified criteria, while strengthening protection against security threats. As a result, access control becomes more precise, security remains optimal, and access management can adapt to the evolving needs of your business

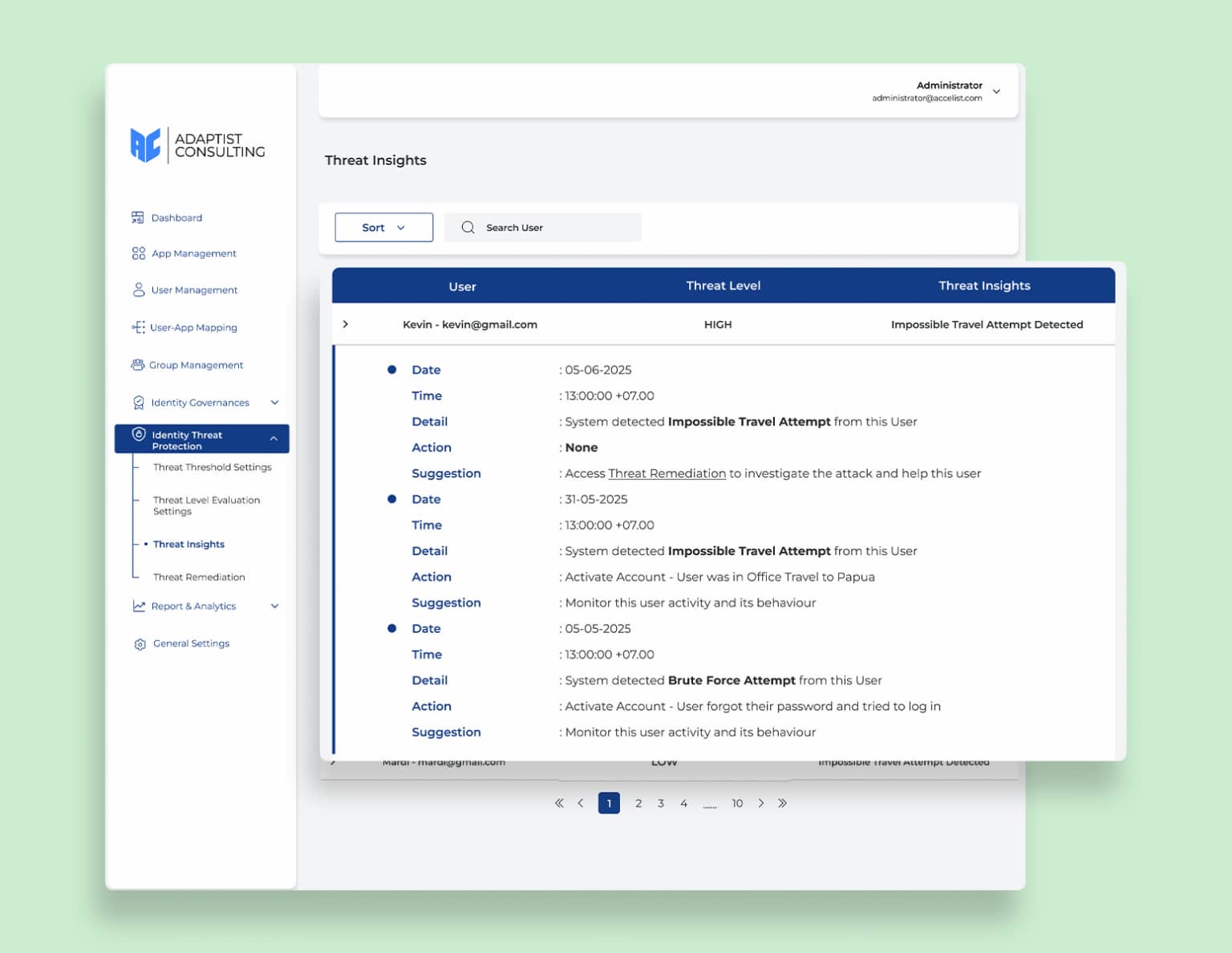
Visibility
Threat Insight
Get comprehensive visibility into potential security threats with Threat Insights. This feature automatically collects and displays information from threat level assessments to incidents detected by the system. With this capability, organizations can identify threats early on, monitor risk levels in real time, and take preventive and remedial action more quickly. As a result, security teams have more proactive control, optimal system protection, and risks can be minimized as threats become more complex
Visibility
Threat Insight
Get comprehensive visibility into potential security threats with Threat Insights. This feature automatically collects and displays information from threat level assessments to incidents detected by the system. With this capability, organizations can identify threats early on, monitor risk levels in real time, and take preventive and remedial action more quickly. As a result, security teams have more proactive control, optimal system protection, and risks can be minimized as threats become more complex

Other Features
Expert guidance on compliance with security standards and regulations
Authentication Method
Password Rule
Self Service Access Request Rule
User Lifecycle Activity Report
Threat Threshold Settings
Threat Remediation
Reasons to Choose Adaptist Prime
Efficient, Secure, and Seamless Access Control
Holistic Solution
Strengthening Security
Compliance Made Easy
Cost-Effective and Unified
Scalable and Customizable
This Is Not Just Security, This Is Smart Protection
Give your team easy access with Single Sign-On (SSO), while maintaining full control over security through proactive threat detection and flexible access policies
Read the Latest Adaptist Prime Articles
This Is Not Just Security, This Is Smart Protection
Give your team easy access with Single Sign-On (SSO), while maintaining full control over security through proactive threat detection and flexible access policies.










